SatoshiPay
Building a Payment Future for Human-AI Coexistence
Satoshi as the Global Unified Unit of Value Exchange
Satoshi, the smallest unit of Bitcoin, not only embodies the original vision of peer-to-peer electronic payments but also paves the way for a future where humans and AI coexist in an integrated economic ecosystem.
By adopting Satoshi for pricing and transactions, Bitcoin transitions from a store of value to a global, intelligent payment tool that serves both carbon-based humans and silicon-based AI entities.
Advantages of Satoshi Payments
Transparent, low-cost, and decentralized
Technical Solutions
Cross-chain mapping, smart contract integration, and stability enhancements
Ecosystem Applications
Spanning DeFi, robot economies, digital content payments, and beyond
Join Us
Help build a Satoshi-powered future economy and share in the decentralized era’s rewards
Technical Architecture
SatoshiPay Multi-Layer Taproot Security Mechanism
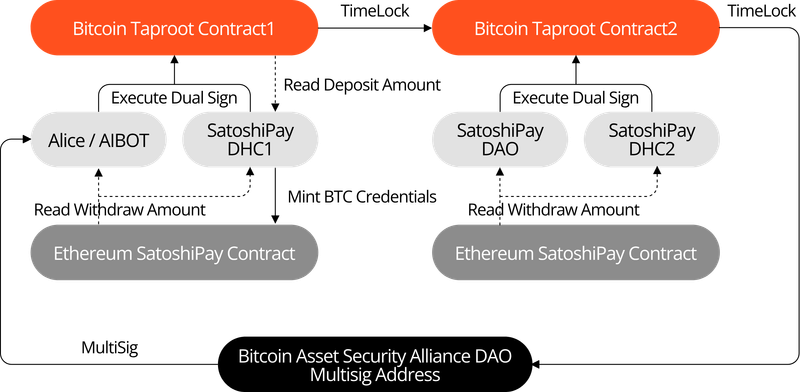
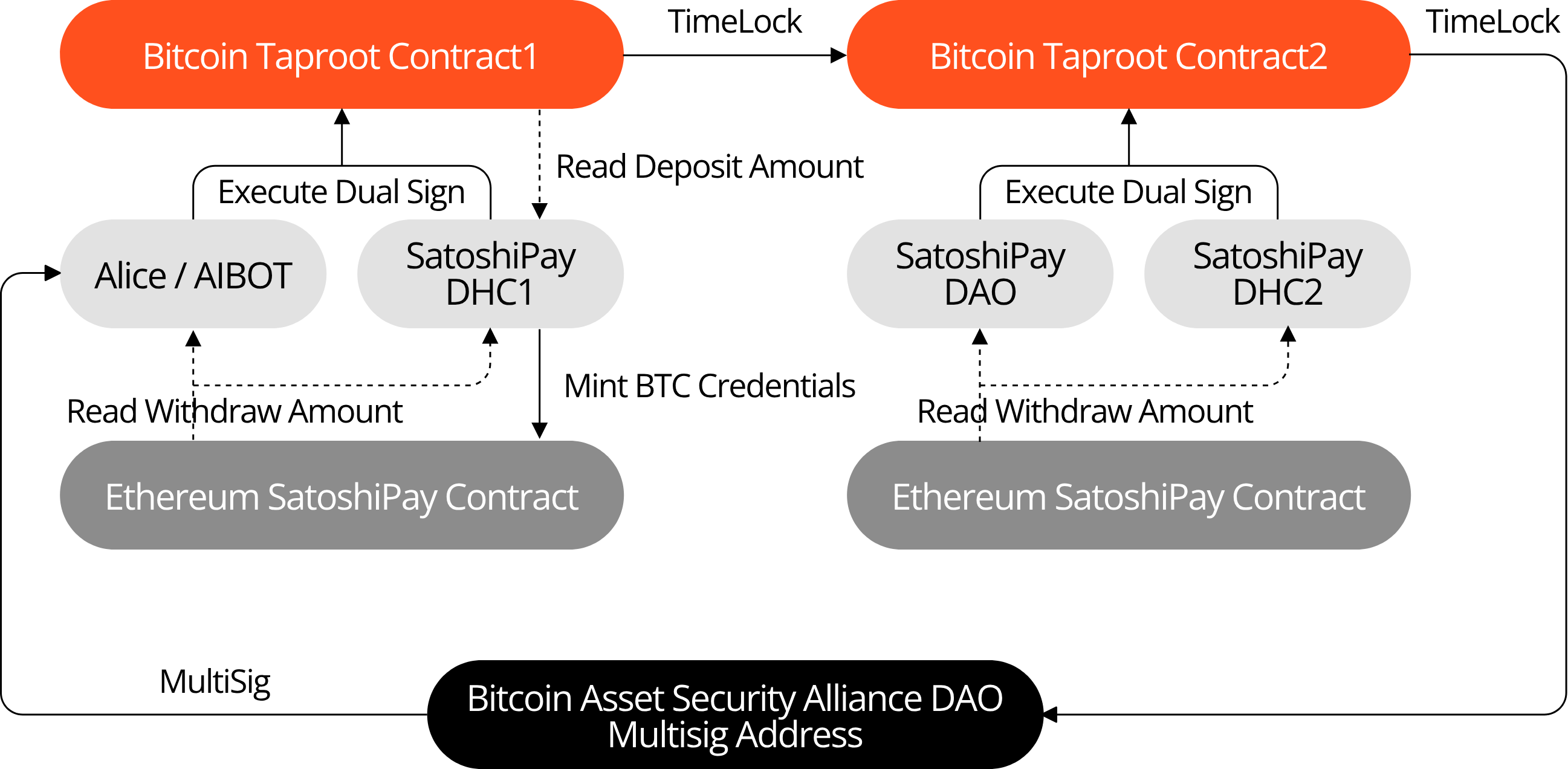
To further enhance security, SatoshiPay employs a multi-layer Taproot security mechanism based on DHC (MPC + ZK + TEE). This advanced mechanism provides SatoshiPay users with robust self-custody capabilities while ensuring asset security even in extreme scenarios, such as private key loss or system attacks.
Security Design & Key Countermeasures
By applying the DHC multi-layer Taproot mechanism to the SatoshiPay project, the system not only enhances the flexibility of asset management but also strengthens security measures.
Response to Private Key Loss
In the event of private key loss, a time-lock mechanism is automatically activated. After the lock period ends, the user’s assets are transferred to a more secure account, ensuring that the assets are not permanently inaccessible.
Prevention of System Failures
If the DHC system encounters systemic issues or failures, SatoshiPay provides users with an emergency escape route through multi-layer management and time-lock mechanisms, ensuring users retain ultimate control over their assets.
Defense Against System Attacks
Even in the case of an attack, attackers cannot gain sole control or steal assets from user accounts. The multi-layered time-lock and signature mechanisms provide robust defense capabilities.